Brand new feature out in public preview, and here is how to manage it using Graph. The documentation is already quite decent.
First of all, there is a set of new Azure AD roles available, and Global Admin cannot manage security attributes by default:

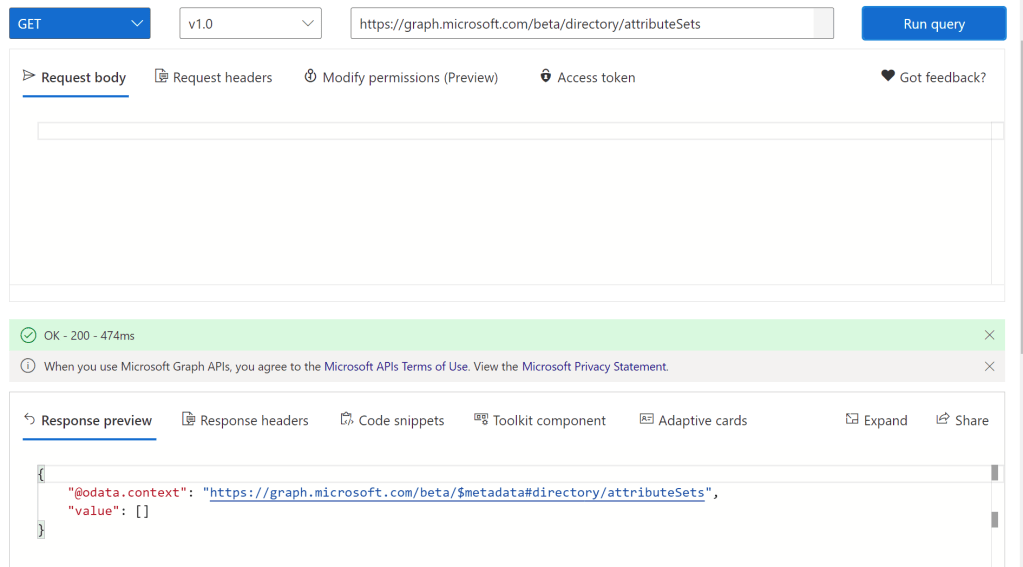
A new Graph endpoint (https://graph.microsoft.com/beta/directory/attributeSets) exists, that returns a list of all attribute sets, currently none:
We can now create a new attribute set as follows:

And we can now add a new attribute to this set:

We can now find the attribute set in the Azure AD portal:


Through the GUI, we can now add the EmploymentEndDate attribute to our user:

But how do we address this using the Graph, without any documentation?
UPDATE: The following now also works using Graph Explorer
Tried the following urls without success:
https://graph.microsoft.com/beta/users/286253f5-9f72-4c44-b361-39177d98266b?$select=customSecurityAttributes
https://graph.microsoft.com/beta/users/286253f5-9f72-4c44-b361-39177d98266b/customSecurityAttributes
As you can see, the request succeeds, but returns empty. Argh! But I can find things through the Azure Portal, that uses the Graph!

Trying with the access token from the Azure Portal works just fine:

So, it seems as though the Graph endpoints are not behaving as expected, with the Graph Explorer yet? Tried checking scope and stuff, but no cigar.
When it comes to the way we manage the custom security attributes on user accounts, I found some interesting deleted content on Github:

Let’s try:

Also erroring out, but let’s try the same request using the token from the Azure Portal:

And this actually ended up working:

So, I am sure this is something that will be fixed soon, and documentation for the endpoints up and running! 🙂
UPDATE: This now also works using Graph Explorer
Marius,
Thanks for pointing out the error with the Graph Explorer. We are fixing the regression soon. Appreciate you taking time to write the blog post. we will update you as soon as the issue is fixed. It would be great if you can update the blog post once we fix this.
Siva M (on behalf of Microsoft Azure AD team)
Thank you! I will 🙂