In my previous blogpost, we dug into how to create the different object types used by agents, more specifically Agent Identity Blueprints, Agent Identity Blueprint Principals, Agent Identities and Agent Users. Now we will try to authenticate as them, and also see what our logs say, so we can detect usage!
Continue reading “Digging deep into Entra agent identities – #2”Digging deep into Entra agent identities – #1
Agents are on everyone’s lips these days. Many of my customers complain that they lack knowledge about how agents interact with their environment, how they sign in, how they act on behalf of their users and they have no clue how to govern them. To be honest, neither do I, so I will be writing a blog series where I dig deep into the realm of agents. Let’s go!
Continue reading “Digging deep into Entra agent identities – #1”The problem of synchronizing pictures from HR to Entra ID / Microsoft 365
Just recently, I had a customer that wanted to synchronize photos for their employees from HR to Entra ID. Here is my experience on this issue, as it was surprisingly difficult to do it “properly”.
When I do integrations like this, I want to make them stateless whenever possible, as the complexity is just so much lower with no state to manage at all. After digging around the Graph endpoint documentation and doing some testing, I found that when we upload a new picture, Microsoft is doing some kind of processing of the image data that we upload, removing metadata and saving it as JPEG.
Continue reading “The problem of synchronizing pictures from HR to Entra ID / Microsoft 365”Mass reconciling / reprocessing access packages into groups
I just had a customer where there were around 3000 access package assignments that has not successfully added users to groups, for some reason. The way to fix this is to find the assignment and click “Reprocess”:
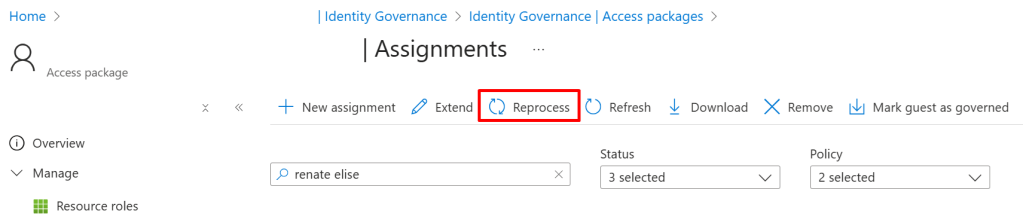
Clicking this button thousands of times is not really how I wanted to spend my evening, so we therefore wanted to figure out which users were affected, and triggering a reprocess for all of these.
Continue reading “Mass reconciling / reprocessing access packages into groups”EntraIDAccessToken, our open module for simplifying Entra ID authentication in your PowerShell scripts and modules
Ok let’s say you are building a new PowerShell module or script and you would like to be able to run it on Windows virtual machines locally in your own datacenter, in Azure Functions, in GitHub Actions, in Azure DevOps Pipelines, in Automation Accounts or any other method of running PowerShell – this is perfectly possible, but how can you have it authenticate to Entra ID without a gazillion lines of code? Any how do you test that each scenario actually works? I present to you EntraIDAccessToken – a free and open module for authenticating to Entra ID, both for Microsoft Graph and any other integrated API.
Continue reading “EntraIDAccessToken, our open module for simplifying Entra ID authentication in your PowerShell scripts and modules”Extracting the results of access reviews in Entra ID
So, you have completed your access reviews for a gazillion groups or access packages in Entra ID, and now would like to show off the result to management? No problem, we can simply dump the results to Excel and do whatever we’d like with them! Let me show you how:
Continue reading “Extracting the results of access reviews in Entra ID”Converting AD groups to Entra ID groups
Finally, the public preview of Group Source of Authority is out! What does this mean for you and me? Well, you can take any number of the groups you are currently synchronizing from Active Directory to Entra ID (which are currently read only in Entra ID), and make them writable in Entra ID. And you can even have turn the solution upside down, having Entra ID update the AD group when members are added/removed!
Let’s dig into this feature!
Continue reading “Converting AD groups to Entra ID groups”Finding which attributes are used by criteria groups in Entra ID
Here is a short script that gets all criteria groups from Entra ID, creating a report over which attributes are in use:
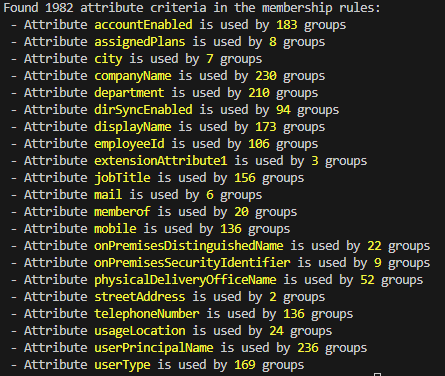
Assigning all users in a group to an access package
Quick reference blogpost here 📝 This is how to take all members of an Entra ID group and assigning them to an access package using PowerShell.
Continue reading “Assigning all users in a group to an access package”Accessing resources cross tenant using managed service identities
Up until now there has been no good way to have a managed service identity on tenant A granted access to resources or graph scopes in tenant B. Finally there is a way to achieve this!
There is a little caveat though, and that is that you will still need another app registration, but by using this new preview, we no longer need client secrets or certificates. Let’s have a look at how this works!
Continue reading “Accessing resources cross tenant using managed service identities”